CERT-In cautions against ransomware ‘Akira’ attack
Context:
According to the most recent advice from the nation’s official cybersecurity office, an Internet ransomware virus called “Akira” has been discovered in cyberspace. This virus encrypts data and takes users’ sensitive personal information in order to demand payment.
What is Akira Virus?
- A particular kind of ransomware that targets and infects computers is called Akira.
- Its primary goal is to encrypt data on infected devices so that users cannot access it.
- Akira manipulates filenames by adding the “.akira” extension to the encrypted files after the contents have been encrypted.
- The malware goes one step further after being executed by wiping out “Windows Shadow Volume Copies” on the targeted device. Users can restore files to earlier versions using this backup feature in Windows. The victims will have a harder time recovering their files if these copies are deleted.
- Double extortion is a tactic that Akira uses that is becoming more and more popular among ransomware outbreaks. In this method, the attackers steal sensitive data from the compromised system in addition to encrypting the victim’s data.
- If the victims fail to pay the required ransom, the attackers threaten to post the stolen data on the dark web.
- The risk of disclosing the stolen data increases the pressure on the victims to pay the ransom.
How does the Akira Virus affect the software?
- Delivery Methods:
- Akira ransomware can enter computers through various means, such as:
- Malicious email attachments or links.
- Pirated software websites.
- Peer-to-peer (P2P) networks.
- Free file hosting sites.
- Third-party downloaders.
- Propagation:
- Cybercriminals may utilize Trojans and phoney software upgrades to spread the Akira ransomware to unaware users.
- The infected file is downloaded and executed by a user unintentionally, and the Akira ransomware then starts to attack.
- Encryption of Files
- Files located in various hard drive folders on the victim’s PC are encrypted by the Akira ransomware.
- Without the decryption key, the encryption process makes the files inaccessible to the user.
- To keep the operating system functioning, it seems to restrict some system directories from encryption:
- Excluded directories have an.exe,.dll,.msi,.lnk, or. sys file extension.
- System folders in the Windows, System Volume Information, Recycle Bin, and Program Data directories are among those that are excluded.
- Laterally moving:
-
- The Akira ransomware can move laterally to additional computers in the network after infecting just one.
- This lateral movement seeks to spread the infection to workstations and servers that are linked to the same network.
- Identity theft
- To increase its network rights, the virus tries to obtain Windows domain admin credentials.
- The Akira ransomware can spread throughout the network and increase its scope and impact by obtaining admin credentials.
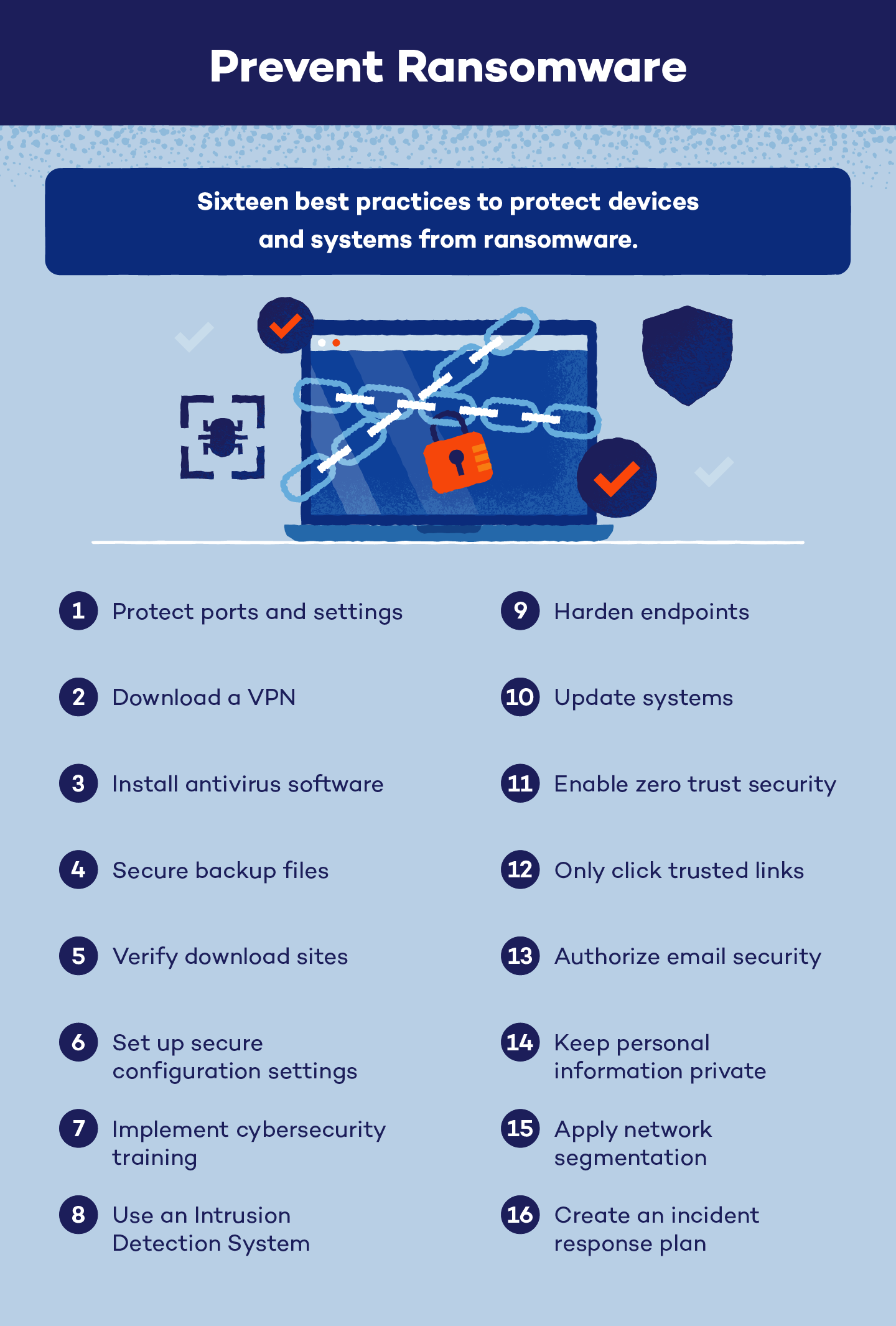
How to protect yourself from ransomware infections?
- CERT-In’s Objectives
- The primary technological department in India that handles cybersecurity incidents is called CERT-In.
- It gathers, examines, and disseminates data on cybersecurity risks and weaknesses.
- To stop or lessen cyberattacks, the agency publishes alerts and advisories at the appropriate times.
- For a successful response to cyber incidents, CERT-In coordinates with a variety of stakeholders, including government entities, businesses, and worldwide CERTs.
- In cybersecurity emergencies, it aids in incident handling, response, and recovery.
- The company carries out research and development to improve all-around cyber resilience in India.
- Be Wary of Email Links and Attachments:
- Malicious email attachments and URLs are common ways that ransomware spreads.
- Do not click on links or open attachments from senders who you are unsure of.
- When receiving unexpected emails, double-check the sender’s credibility and proceed with caution.
- Download only from trustworthy sources:
- Download software and files only from trusted websites and authorised retailers.
- Refrain from downloading software or clicking on adverts from dubious or suspicious websites.
- Update software regularly:
- Update your operating system, software, and antivirus software frequently.
- Security patches that close holes that hackers could exploit are frequently included in updates.
- Use Multi-Factor Authentication (MFA) and strong passwords:
- Incorporate upper- and lowercase letters, digits, and symbols into your password policies.
- To provide an extra degree of protection, enable Multi-Factor Authentication (MFA) whenever possible.
- When logging in, MFA requires users to submit additional verification, such as a one-time code.
- Backup important data:
- Regularly backup important data to external drives or a secure cloud storage platform.
- To prevent ransomware from encrypting backups in the event of an attack, keep them offline.
- To reduce data loss in the case of a ransomware attack, make sure backups are current.